Good vs Evil : Hidden Worlds Of Scam Baiting, Scams & Scammers
Scams are on the rise year by year and so do the number of scam baiters (aka the digital vigilantes). Over the past 12 months alone, fraud has escalated to “epidemic” levels in the US. In fact, it has now become a “national security threat,” costing up to £190 billion a year, thus creating an urgent need for an institutional response. And on the other side, experts, amateurs, and enthusiasts are flocking together, scam baiting. Working in unison, hidden, and fighting the good fight to keep you safe. Hidden wars are being fought right now, battles of wills, using tricks, social engineering, and tech-know-how. You could say, this is the modern age battle of good vs evil, the knight crusaders, marching on evil.
The struggles and failure of police to keep up with constantly evolving fraudsters have led to a drastic increase in scamming cases. This in turn has influenced the rise of scambaiting. Realistically, only 4% of fraud-related cases reported to Action Fraud have been solved, meaning that 96% of cases remain unsolved, according to 2018 Which report.
Wow, right?

Online vigilantes known as scam baiters are taking matters into their own hands. But what is scambaiting? How do they do it? Is it wrong or safe to bait scammers? And what is the best scambaiting site or tool to search or report a scammer?
Let’s take a look.
What is scam baiting?
Scam baiting is a form of digital vigilantism used against fraudsters with the sole purpose of preventing them from scamming the real victims. The most basic form of scambaiting is usually about wasting scammers’ time by posing as a victim. However, the most effective and probably influential form is gathering as much information as possible, such as scammers’ emails, banks accounts, addresses, etc., and forwarding them to the relevant authorities.
Scam baiters are internet alias, and they usually voice different characters to be able to lure their brays into taking the bait. They are professional and experts in their field as they can change their voices and create untraceable emails and completely fake account that seems 100% real.
Surprisingly, some scam baiters have incredible technical skills; for example, Pierogi utilizes his cybersecurity expertise. With these excellent abilities, they can easily manipulate scammers and even hack into scammers’ emails and send warning messages to their potential victims. They are our superheroes because they keep them occupied to limit their damage. They also create awareness and warning by posting videos dealing with these scammers, thus educating us.
Different types of scammers
Scamming practices comes in different forms, meaning there are different types of scammers, which include:
- Phishing scammers are fraudsters who work their scams with the aim of obtaining sensitive information from their victims. These scammers usually employ fear and urgency to convince their victims to share their information.
- Pet scammers: This type of online scammers usually utilize social media platforms or websites to sell different animals that actually do not exist.
- Romance scammers: We all crave love, and nowadays, social media has made it really easy to get a new lover. However, you should be careful of romance scammers creating fake online relationships with their victims with the aim of blackmailing them.
- Crypto scammers: These are mostly the scammers that work on the crypto-related market. Mostly they come with short-term lucrative investment ideas that if you invest X amount of crypto, you will get big payouts with guaranteed returns. They also promise free money and groundbreaking achievements or claims with little or no explanation.
- Pension scammers: If someone ever reaches out to you and gives you attractive-sounding promises that involve transferring your pension savings, then you’re being scammed. Report this kind of scammers to avoid more spammy calls from them.

Why do people scam bait?
There are several reasons why scam baiters do what they do. Besides, their main goal for being scam baiters is to prevent them from exploiting innocent victims. Rosie Okumura explains that “I waste their time, and now they’re not stealing from someone’s grandma.”
Okumura is a 35-year-old LA-based scam baiter who scams, disrupts, and exposes the world’s top scammers on her YouTube channel.
Unfortunately, the fact is, scammers are becoming clever day by day and coming up with better tricks that improve the efficiency of their work. In May 2021, Ofcom even warned that scammers can now “spoof” legitimate phone numbers, which increases their chances of success. Additionally, they can make good calls and deceptively pose as good as if they are actually calling from your bank.
Notably, phone and text fraud was up by 83% during the pandemic, which shows a sudden massive increase in scamming. Therefore, the only superheroes who can try and cop up with the growing field of fraudsters are scam baiters, which is why they are important. But what are the reasons behind scambaiting, and what actually motivates scam baiters to do this?
What actually motivates scam baiters to do this?
Well, according to Rosie Okumura, here are a few reasons why she chose to become a scam baiter:
- Getting scammed or somebody close to them gating scammed. Rosie became a scambaiter after her mum (in her 60s) lost $500 to a scammer.
- Entertainment “a lot of it is entertainment – it’s funny, it’s fun to do, it makes people happy.”
- To create awareness: she says some people have emailed me saying, “Oh, thank you so much, if it weren’t for that video, I would’ve lost $1,500.”
- Educating people on how to deal with scammers
Overall, education and prevention are crucial to dealing with scammers, says Okumura. She also believes that you can change a few scammers’ hearts and make them choose the right path.
With that said, let’s now define whether scambaiting is wrong or right.
Is scam baiting wrong?
There is no doubt that scambaiting is good in reducing online fraud, but is it wrong to scam bait?
To some extent, yes, but deeming whether it’s wrong or right thing is dependent on the methods used by a scam baiter.
What I mean is, some scambaiting methods are ideally good and safe, and they will do their intended purpose, which is to reduce online fraud without any harm. However, some strategies employed by some scum baiters are dangerous may inflict damage or humiliate scammers. Therefore, this means that scambaiting can, in fact, cause more harm than good, thus making it wrong. And as the saying goes, two wrongs don’t make right!
Is it safe to Scam bait fraudsters?
Generally, yes, it is safe.
If you are planning to scam bait a scammer, then there are several things you need to do to ensure your safety. These things include using fake accounts, which comprises of:
- Fake ID information
- A Fake address
- Fake phone numbers
- Fake names
Unless there are really good reasons to use your factual information, it is advisable to use all fake information that would seem ideal from the scammer’s point of view. Generally, for me, it is usually ideal to use existing online fraud-dedicated communities, such as r/scambait on Reddit or 419eater.com, to bait a scammer.
Tips on scam baiting (Scam baiting strategies)
There are several effective ways to find a scammer; some are basic, some are humiliating, and others are fun and entertaining. Ideally, the primary strategy of scam baiting is to lure a scam baiter by initiating a trap to which a scammer will fall victim.
Here are some of the common categories of scambaiting strategies that scam baiters use:
- Straight bait – This strategy is one of the most basic methods of scambaiting scammers. It involves emailing swindlers and pretending to be real victims. You can use this method to ask fraudsters to fill an imaginary questionnaire that is time-consuming. This trick will keep them occupied for quite some time, thus limiting them from scamming actual victims.
- Phone bait – Phone bait is another popular method used by scam baiters, and it involves getting fraudsters to call you or calling scammers. Scam baiters sometimes incorporate imaginary questionnaires as well to keep their scammers at bay.
- Cash bait – This is an illegal strategy of trying to scam scammers by getting them to send money in exchange for something.
- Freight bait – Getting scammers to actually pay for the shipping fee of something of value to scam baiter in return for something (fake).
- Safari bait – What’s better than getting scammers to travel for no reason by getting them to think they are going to get what they are looking for in a place they are going. Well, this method isn’t ethical, but what they are doing isn’t either. This method is usually ideal when you want to discover a scammer’s identity in order to report them to the responsible authorities.
- Church bait – Getting scammers to join your fake or real church so that you can meet over there.
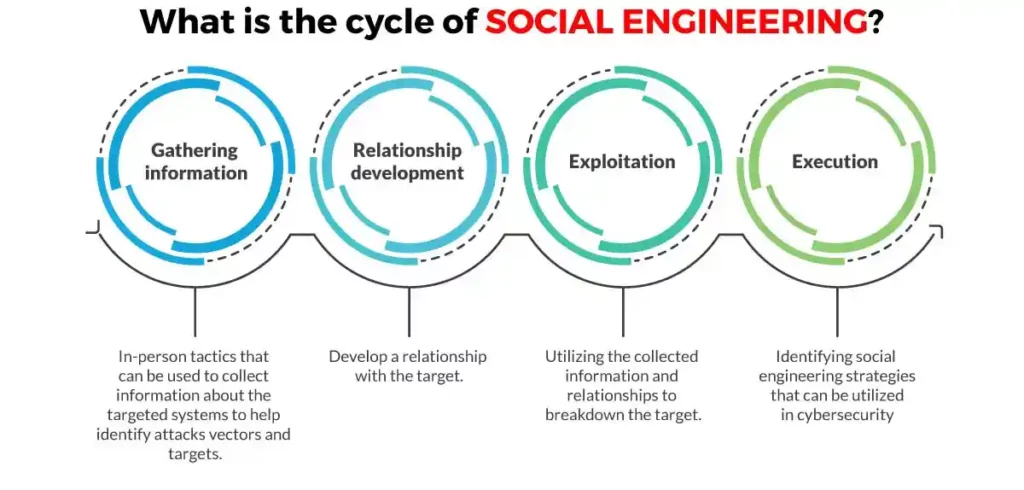
Strategies for scam baiting:
Besides categories, two forms of strategies employed by scam baiters to scam bait scammers exist as well. One is anti-scam work, which focuses on creating awareness. The other form involves incredible story-plots that are done repeatedly against the same scammer.
Anti-scam work:
- A “big order” – Aims at reporting scammers using stolen credits card to make big orders.
- Scam Alerts – This is about posting formats of emails messages or recorded phone calls used by scammers online to create awareness.
- Trophy hunting – This strategy aims at getting scammers to send photos or videos of something.
Incredible story-plots of scam baits
These strategies are mainly about wasting scammers’ time or reporting phony websites so that they can be hunted down. Ideally, the trick employed here are usually done repeatedly for some time, and it involves strategies like:
- Romance scam seeking are romance-related scams that comprise ‘honey trap’ and ‘neutral profile,’ and ‘vinegar trap’ sub-strategies.
- Additionally, wasting their time via calls or long email messaging
- Safari Agents
- Reporting bank accounts used by scammers
- Inbox divers which involve logging into scammers emails and sending warnings to their victims
- Reporting phony websites used by scammers
Top 7 Famous global Scam Baiter influencers
- Michael Berry is a founder of a scambaiting website 419eater.com, and he goes by the alias Shiver Members.
- Rosie Okumura 35-year-old LA-based scambaiter and YouTuber – IRLrosie
- Kitboga an American scam baiter against scams steered over the phone. He is also YouTuber and Twitch streamer
- Ansar Hamed is another top scambaiter famously known for his YouTube videos on the scam-related niche.
- Jim Browning is a London-based YouTuber and a software engineer from Northern Ireland.
- Pierogi, famously known as Scammer Payback, is an American YouTuber who focuses on scambaiting scammers
- ScammerRevolts is an internet alias known for messing around with tax revenue, refund, and tech supports scammers
Where should I report a scammer?
There are various places where you can report scammers, and each region or country has its own ways of dealing with scammers. The problem is, each country has its own way of reporting scams and Scammers. The problem is, no one really knows where the scam is based! Solution? There is a Global Scam Database for all countries to report and share this information too. It can also be quickly and freely searched by anyone. You can report & search by username, website, email address, phone number, and bitcoin address. The website is called ScamSearch.io, and it’s only a few months old but already has over 5 million recorded scammer details!
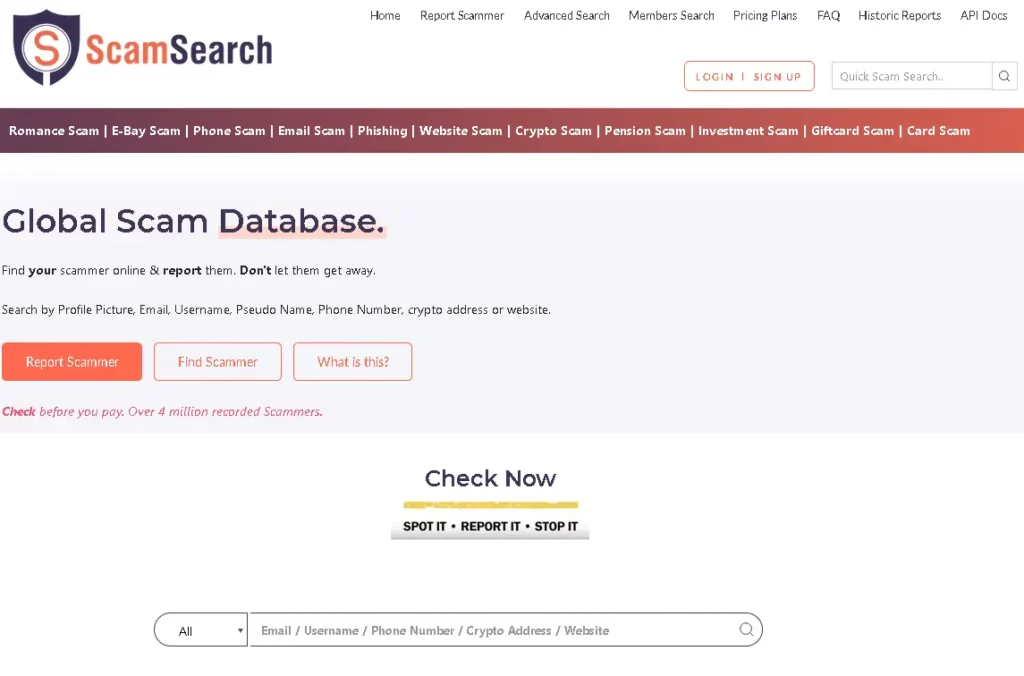
With Scam Search, you have free access to a global scam database. This database will allow you to search and find your scammer online and report them. It is quite easy to use this database; you can simply:
- Search by profile picture
- Search by email
- Or Search by username
- Search by pseudo name
- Search by phone number
- Or Search by crypto address, or
- Search by website.
So, we are not saying just report to ScamSearch. You should also inform your local enforcement, but to be honest…the way it’s going, your local enforcement team is going to be using Scam Search to check worldwide reports on your scammer, to start the investigation.
Scambaiting & anti-scam tools
In the act of internet vigilantism (scambaiting), scam baiters often provide details on the anti-scam tool that a person can use to avoid falling victim to scam attacks. Here are some of the anti-scam tools.
Tools
- ScamSearch- Scam Search is a free public database of reported scammer data showing their email addresses, phone numbers, usernames, websites as well as crypto addresses. You can sign up and be your own scam detective by using advanced features in ScamSerach.
- Scammer phone number lookup- It is possible to do a scammer phone lookup using various search engines that offer free or paid services. These services don’t require any special skills; you can use them whenever you want to obtain info about an unknown number. Examples of phone number lookup platforms are Truthfinder and instant checkmate.
- Email scammer Check-You can use a reverse email search service, an online tool that assists users in finding out who is in contact with them via email, especially from unknown email addresses. Examples of reverse email lookup websites are UserSearch.
- Website scammer Check- There are different online platforms that allow you to check if a website is a potential threat, such as WHOIS(ICANN). WHOIS is a website checker that allows you to see info about any domain once you enter a URL and click the option “Lookup.”
‘Gathering and saving evidence’ during a scam bait
Scambaiters use social engineering tactics (psychological tricks) to monitor scammer communication avenues such as emails, text messages, or phone calls in order to gather enough information on how scammers do their operations and potentially save up enough evidence to report the fraudsters.
By diving into scammers’ inboxes, scam baiters can observe their work strategies, investigate cybercrime structure, and warn the public on potential cyberattacks with enough evidence.
According to kronman and Zingerle, scam baiter communities have fashioned their social engineering techniques to scam the scammers. Therefore, undertaking investigation in gathering and saving potential evidence on cybercrimes by accessing the scammer’s inbox and posing as vulnerable victims with fake characters and convincing storytelling strategies.
Rapid growth scams
To fully prepare yourself to scam bait the scammer, you need to know how the scam works.
1. Phishing scam
Phishing is a cybercrime where scammers attempt to collect personal information from victims through emails or text messages. Perpetrators pose as a legitimate organization to lure targets into giving sensitive information like personal identification, passwords, credit cards, and bank details. The collected data is then used to access targeted accounts resulting in both identity theft and financial extortion.
Common traits of phishing emails include:
- Sense of urgency– The common tactic used in scamming is the impression that super deals are time-limited, so victims are urged to act fast. Such emails that show time urgency in giving out personal data should be considered scams and ignored.
- Too good to be true– Scammers use eye-catching offers such as giveaways or big prizes to be won to instantly get the attention of targets. (If an offer seems too good to be true, most likely it is).
- Hyperlinks-A link may be used to direct you to a phishing website upon clicking. The website is usually a copycat of the original website. It’s recommended to manually type the website you wish to visit on a browser instead of clicking on anonymous links.
- Attachments– Don’t openan unexpected attachment sent to you via email; often, they contain viruses or payloads ransomware. Check for the file extension .txt file, which is usually safe to open.
2. Pyramid scheme scam
A pyramid scheme is a rudimentary business model in which members attempt to generate money by solely recruiting new members. The newbies pay an upfront amount up the chain to the participants who enrolled them, and the process continues when they themselves recruit other newer members to the business. Also referred to as pyramid scams, these schemes are considered illegal in certain countries.
The characteristics of the pyramid schemes are:
- The schemes promise huge profit returns in a very short time plan.
- There are no actual sales of the products or services.
- The primary emphasis is to recruit new members.
- Easy money or passive income.
- No evidence of revenue from retail sales.
- Complicated commission structure.
Scammers usually use social media platforms to promote pyramid schemes. The Promoters go to the extent of making the program appear like some legitimate business, e.g., (MLM) multi-level marketing program to easily convince the target crowd of their authenticity. The promoters use money paid by the new participants to pay off the top-level members, who usually are recruits as well. At one point in the future, the pyramid schemes become enormous, and the promoters fail to generate sufficient income from new recruits to pay earlier investors. At this point, people make losses, specifically new investors.
3. Smishing scam
Smishing is also known as “SMS phishing,” is a cybersecurity attack carried out via text message in which a user is tricked into clicking a link and sending personal information to the attacker or downloading a virus or malicious programs into a smartphone.
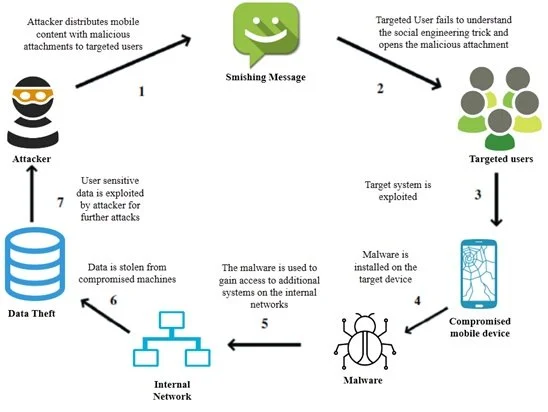
Many smartphones can receive text messages from any number across the world. It is common for most individuals to avoid clicking suspicious links sent via emails. However, not many are aware of taking the same precaution with links sent via text messages.
Smishing is a lucrative approach to attackers for banking details, personal data, and credentials since phone users trust messages received via text over email.
How do Smishing Scams Work?
Scammers send text messages that lure a user into clicking a link or asking the victim to provide a reply. This entails personal credentials to online accounts, financial data, or private details used in identity theft.
Smishers may use a victim’s name or address obtained from a public online tool to make the target think that the message comes from a trusted source. When a scammer uses your name or location in the text, this makes the message appear convincing. The text message shows a link that is directed to a smishers-controlled server, which upon clicking it leads the user to a data phishing site or malware programmed to compromise the mobile device. The malware can now be used to send the user’s mobile phone data silently to an attacker-controlled server.
Example of a Smishing attack
Most attacks come from an automated text message sent using an email address to avoid being detected. The phone number that appears in the caller ID is normally a number that shows an online VoIP service like Google Voice. Therefore it becomes impossible to pinpoint the exact location of the number that sent the text message.
Here is an example of a smisher who lures a victim with an amazon promotion if they provide personal information.
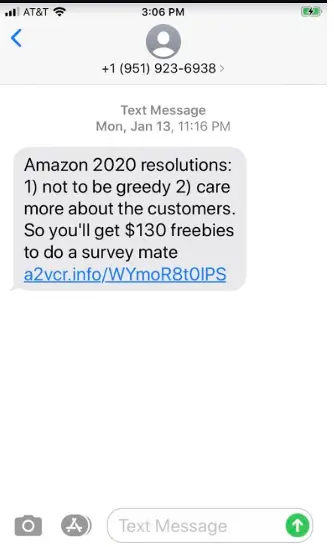
The link attached to the message directs a user to a .info site unrelated to the Amazon website. URLs used in smishing redirects victims to a page linked to an attacker-controlled server that attempts to collect personal information.
How to protect yourself from Smishing Attacks
Basically, protection against smishing depends on a user’s ability to identify an attempted smishing attack. Smishing messages pose a threat only if the victim clicks on the link or sends the attacker private information.
Tips for identifying or scambaiting smishing and avoiding falling a victim:
- The smishing message offers quick cash either by winning lottery prizes or collecting money after entering private data.
- Financial companies will not ask for banks credentials or transfer of money. Don’t send your credit card details, ATM passcodes, or bank details to anyone via text message.
- Message sent from a number with a few digits most likely comes from an email address which is a sign of scam text, should be avoided.
- Banking details stored in a mobile device are a target for scammers. Avoid saving this sensitive information on the device. In an event where an attacker installs malware on your smartphone, the banking credentials could be easily accessed.
- Also, It is good practice to avoid responding to unfamiliar numbers.
- Always report a case of possible smishing to telecom providers to protect other users.
4. Vishing Scams
Vishing or “voice phishing” is a scam technique used to defraud victims to give out private details over a phone call. Nevertheless, the attacker entices the victim in an attempt to get their personal data primarily for financial gain
How does Vishing happen?
The attacker uses a social engineering approach to get the victim to share their personal information and financial credentials, such as account details and passcodes, over a vishing phone call. In fact, “Your account has been compromised” is commonly what the scammers will say and claim that they are from a bank or law entity. Therefore, they might tell you to install the software on your device, which is probably malware—the goal of the scammer is to steal your identity or finances.
Common Techniques used in Vishing
- Wardialing- The attacker uses software to make calls to specific area codes. They use a message claiming to be from an institution such as a bank. And so, When the call is picked up, the automated message urges individuals to share their banking information or social security details. The recorded message may imply that the information needed is to confirm the validity of the victim’s accounts.
- VoIP- VoIP allows scammers to generate fake numbers which are hard to trace. Scammers may create VoIP numbers that seem to be linked to government dependents making it believable.
- Caller ID Spoofing- Similar to VoIP, scammers can hide behind caller ID spoofing. Their names may appear unknown and impose to be legitimate callers such as an agent from the bank.
- Dumpster Diving- This technique allows cybercriminals to dig through dumpsters behind financial institutions and random companies to collect valid phone numbers from these organizations for targeted vishing attacks.
Common vishing scams
Popular scams carried out via Vishing include:
- Compromised bank accounts or credit cards
- Investment or loan offers
- Social security or Medicare scam
- IRS tax scam
How to identify a vishing scam
The following are some signs of a vishing attempt:
- Hysterical sense of urgency.
- The caller asks for private information such as bank account numbers and passwords
- The caller claims to be an IRS, Medicare, or Social Security Administration agent. (These federal agencies will not initiate contact with you unless you’ve requested them to).
How can you protect yourself from Vishing?
- Verify the caller’s identity. Look up the company’s official numbers from their website.
- Don’t answer a call from unknown callers. Instead, let them go to voicemail, then listen to the message and decide whether to call back. Remember caller IDs can be faked.
- Don’t press the button or respond to prompts. You might get an automated message that asks you to press buttons or respond to prompts, and this is a technique often used to scam people.

How to recover from a vishing attack
Say you gave out your financial information to persons you suspect to be scammers, call your banks or credit card provider and request them to block any fraudulent transactions. Also, you might need to change your account details to make sure no one can access them. Additionally, you can use scam baiters to help you discover the man behind the scam
Most common scams
1. WhatsApp scams
WhatsApp is one of the easiest and safest platforms for communication, but that doesn’t stop scammers from reaching their targets. Here are some of the scams you will encounter using WhatsApp.
- Modded version of WhatsApp- Cybercrime experts warned about WhatsApp Mods- an unofficial version that offers additional features to the chat app. They generally carry potential malware into your device. Experts suggest that the malware can launch ads, purchase subscriptions and interject texts. It is recommended to download WhatsApp from the official app store to avoid falling victim.
- Money theft WhatsApp scam- The Chartered Trading Standards Institute (CTSI) has warned users regarding the fraud involving a scammer imposing to be someone you know then asks you for money. The attacker may pose to be a friend or family member requesting financial assistance due to an emergency to entice you to act immediately.
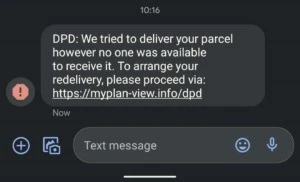
2. DPD scam
Cybercriminals may use DPD to scam people about package deliveries. Scammers send a text that appears to be from DPD saying that a delivery attempt has been made and urges victims to click a link to arrange for redelivery. The link directs you to a counterfeit DPD website asking for personal data and a small amount for ‘redelivery.’
Example of a DPD scam sent via text
Example of a fake DPD website asking for money.
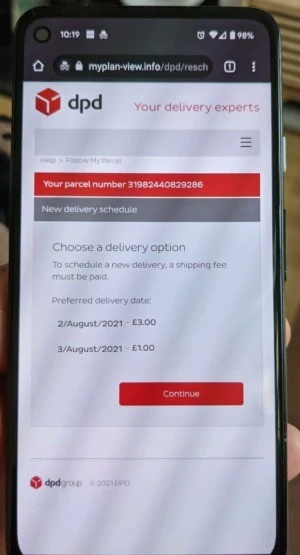
It is recommended to contact the organization directly upon receiving such a text and don’t share your information via text or click links sent to you.
3. Cash App scam
Mobile payment services such as Cash App have become a familiar digital solution to many users on a day-to-day basis. Cash App allows you to make transactions with just a click of a button, and you can link your bank and credit cards to the app. And so, for Cash App users, here is what to look out for.
- Fake Cash App Support
- Cash App giveaway scam
Therefore, to avoid falling victims to a scam, avoid websites that claim to be Cash App support or offer giveaways. Always contact support via the mobile app.
4. Facebook marketplace scams
Scammers use the Facebook marketplace to cash in by stealing money from users. In fact, the openness of the interaction on Facebook creates an opportunity for attackers to trick their victims into a number of scams.
Here is what to look out for:
- Communicating or making transactions outside Facebook should be avoided.
- Counterfeit goods. Look carefully into an item before buying.
- Advance payments. You should not agree to pay for a product before receiving it.
- Fake accounts. Take a look closely at the seller’s profile before buying any item.
- Fake giveaways that phish for information.
Do’s and Don’ts of scam baiting
Let’s take a look at the Dos and Don’ts in scambaiting.
Do’s:
- Use a virtual machine to scambait always.
- Always have evidence of a hidden VM.
- Use fake details such as names, addresses, etc.
- Use fake credit card information. You can use a fake credit card generator to get card info.
Don’ts:
- Do not share your original personal details.
- Don’t use a real machine to avoid syskey.
- Do not scambait using your real phone number.
- Don’t attempt to scam them, i.e., getting money from them.
- Don’t pose to know everything, act like a victim.
Keep up the good fight
With this article, you pretty much have a good grasp of scambaiting and how to do it. You also have some great resources on where to start. If you found this article useful, you may also be interested in these:


